Azure Onboarding - Manual Deployment
This guide is for customers who want to manually onboard Azure subscriptions, management groups, or tenants to Panoptica, without using automated scripts. If you prefer using PowerShell scripts and ARM templates, please visit Azure Onboarding.
The onboarding process is composed of three steps that you complete in the Azure portal: application creation, permissions, and role creation/assignment. Along the way, you'll gather details about your Azure deployment to feed into the Panoptica console, where you'll complete the onboarding process.
Privileges and PermissionsSufficient privileges to your Azure environment are required in order to complete the deployment.
- User must have permission to create a Microsoft Entra ID (formerly Azure AD) application, add a role assignment to subscriptions, and create a custom role.
- Onboarding also requires Read permission to your Entra ID, which requires consent from a Global Administrator in your tenant.
Step 1: Create a Microsoft Entra ID App Registration
- Log in to the Azure portal.
- Go to Microsoft Entra ID (formerly Azure Active Directory) via search, or from the menu to the left.
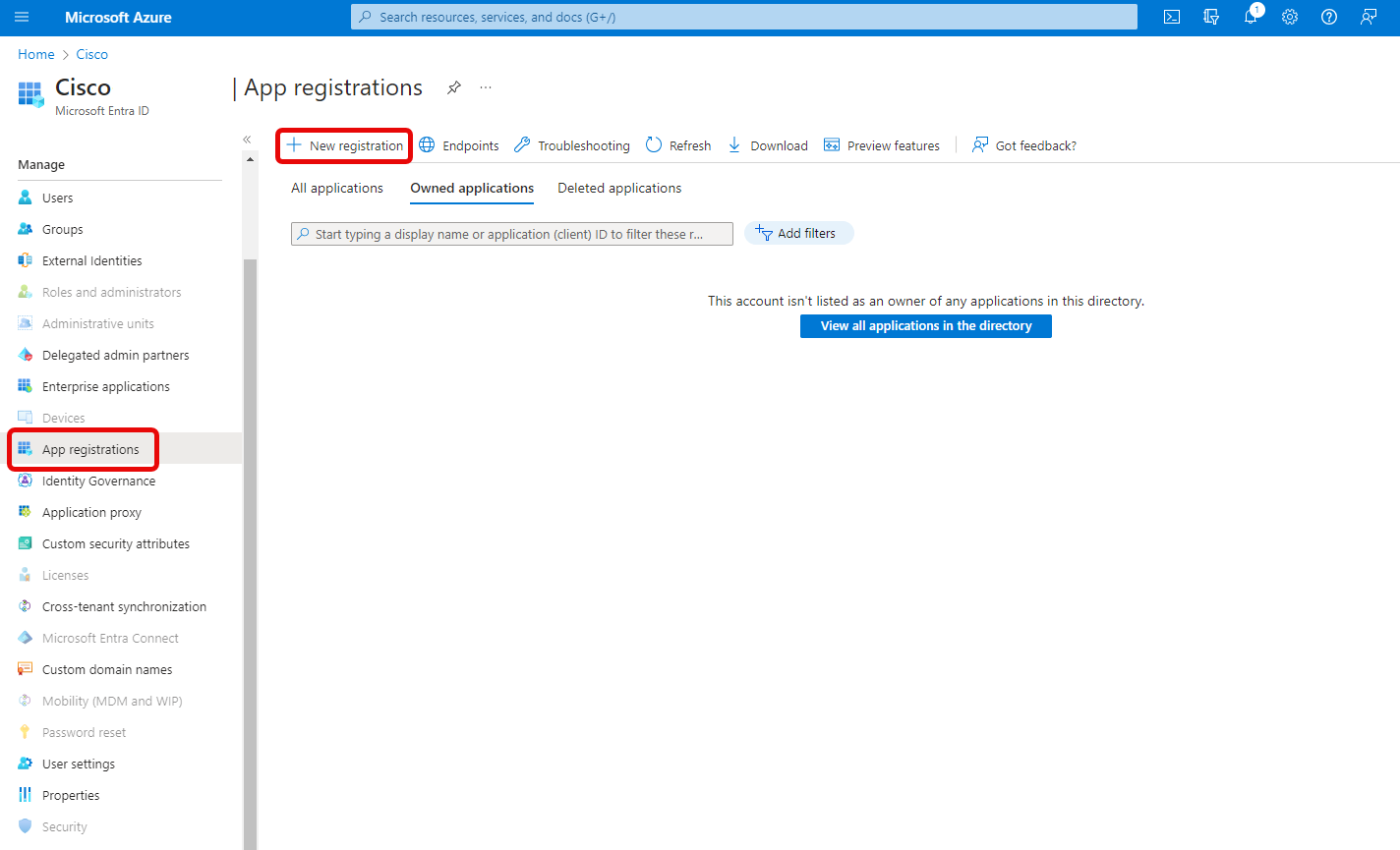
- Click App registrations, then New registration.
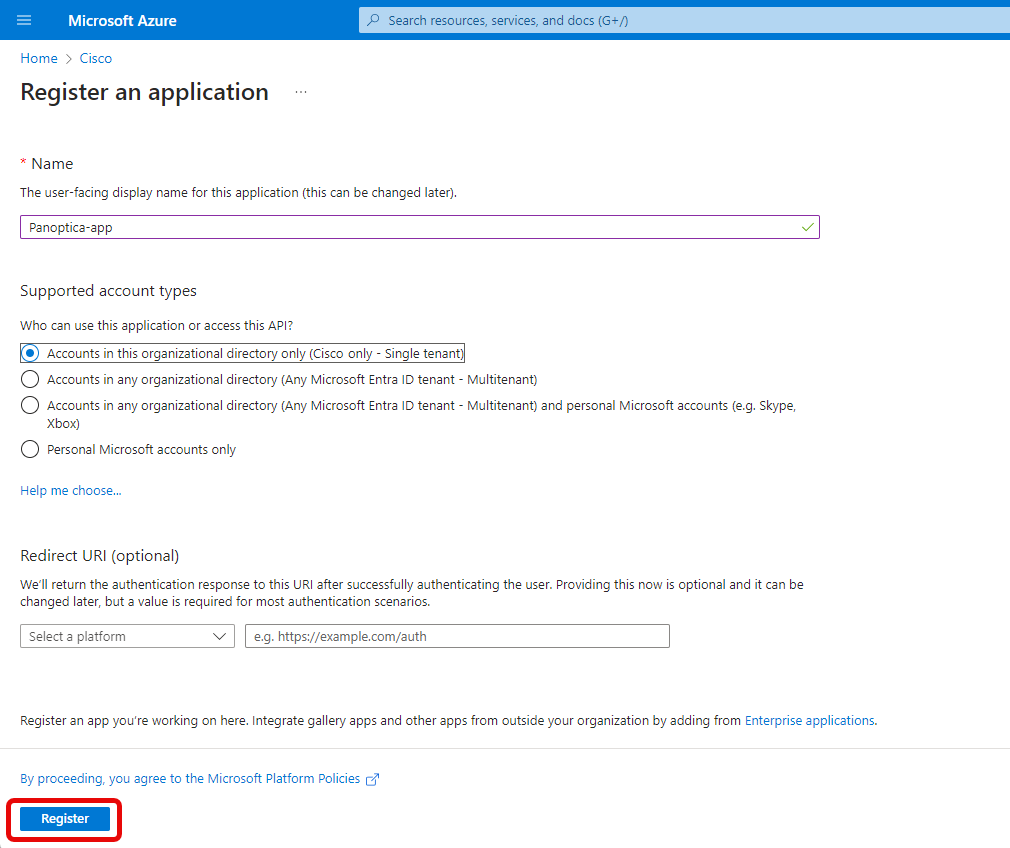
- Choose a logical name for the application, and click Register at the bottom.
IdentifiersOnce the application is created, take note of the identifiers (IDs) that are displayed.
- Application (or Client) ID
- Directory (or Tenant) ID
You will need those values later to connect your application to the Panoptica console.
- Next, choose how you would like Panoptica to be authenticated in your Azure environment. We highly recommend Federated credentials for stability. Panoptica also supports Client secrets, but these need to be renewed periodically; expired credentials will cause the security scans to fail.
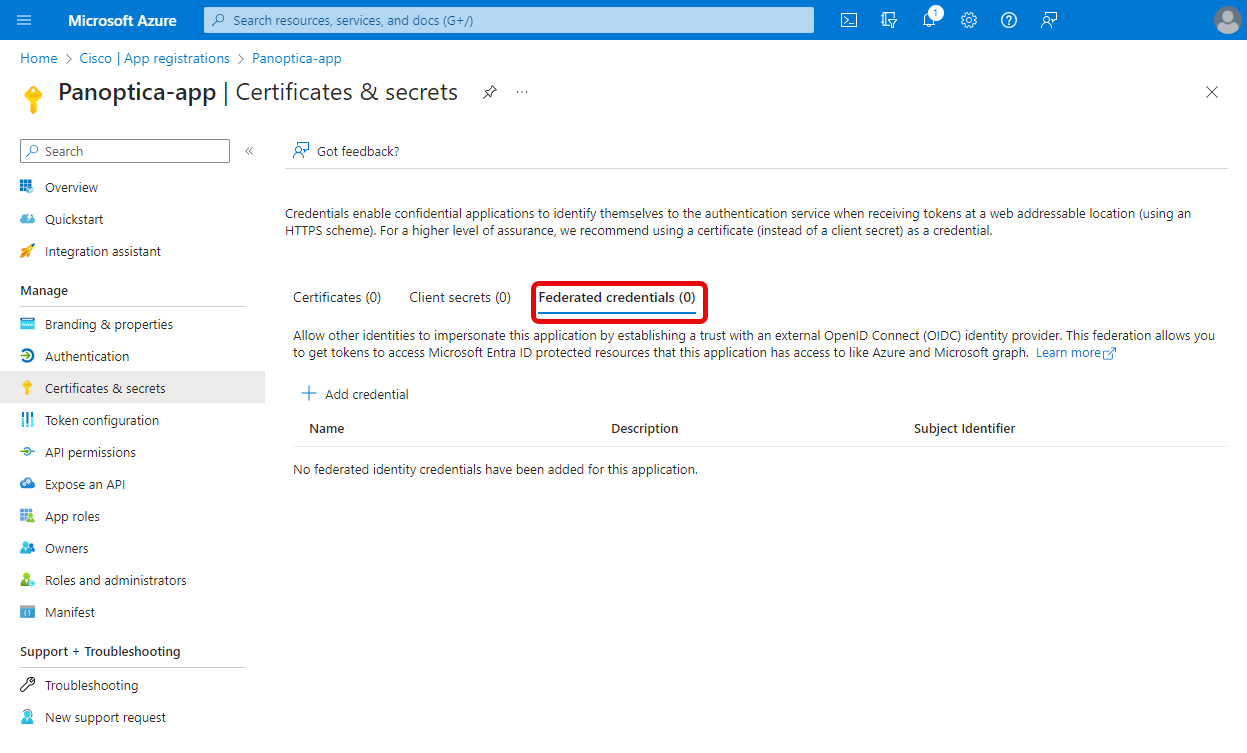
While viewing your application, click Certificates & Secrets in the left-side navigation menu. - Go to the Federated credentials tab, and click Add credential
-
On the Add a credential screen, select Other issuer, and fill in the form as follows:
- Issuer: https://accounts.google.com/
- Subject identifier: 104631297208827230230
- Name: pick a good one
Then click Add
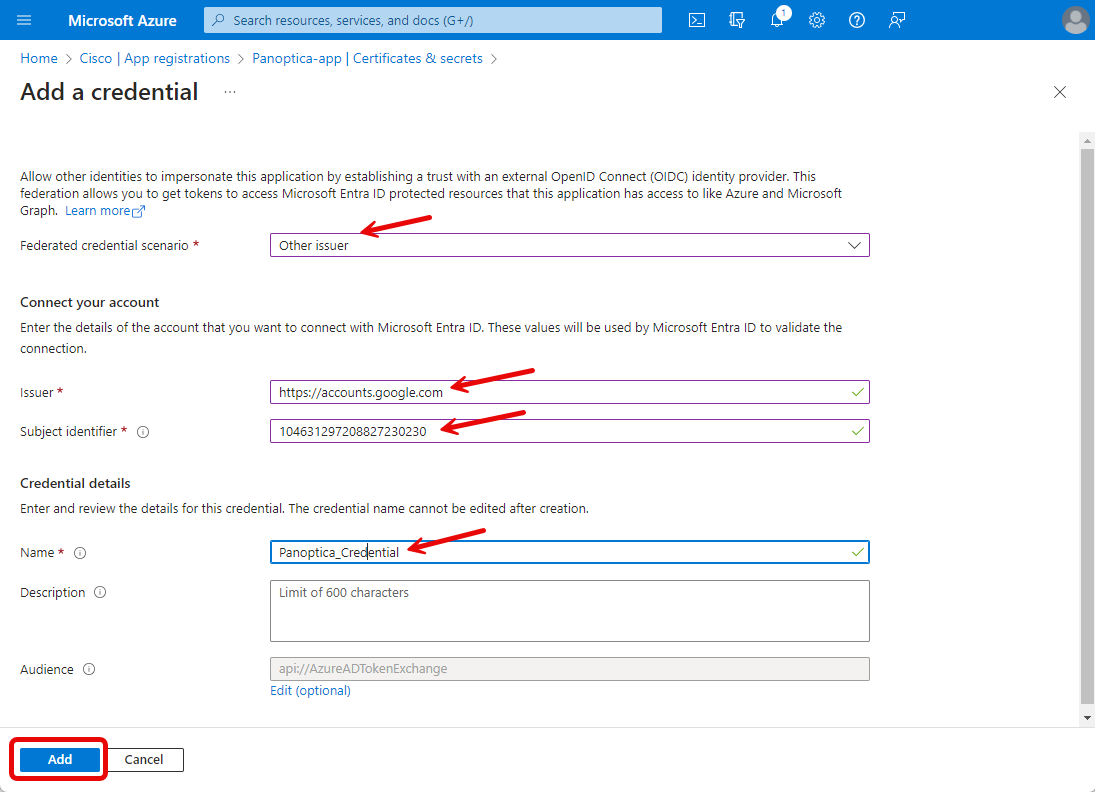
- If you prefer working with client secrets, go to the Client secrets tab under Certificates and Secrets to create one. Copy and paste the value into the Application Secret field on the Panoptica console.
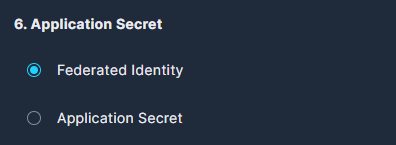
Otherwise, leave the default Federated Identity selected.
Step 2: Grant Azure AD Permissions
-
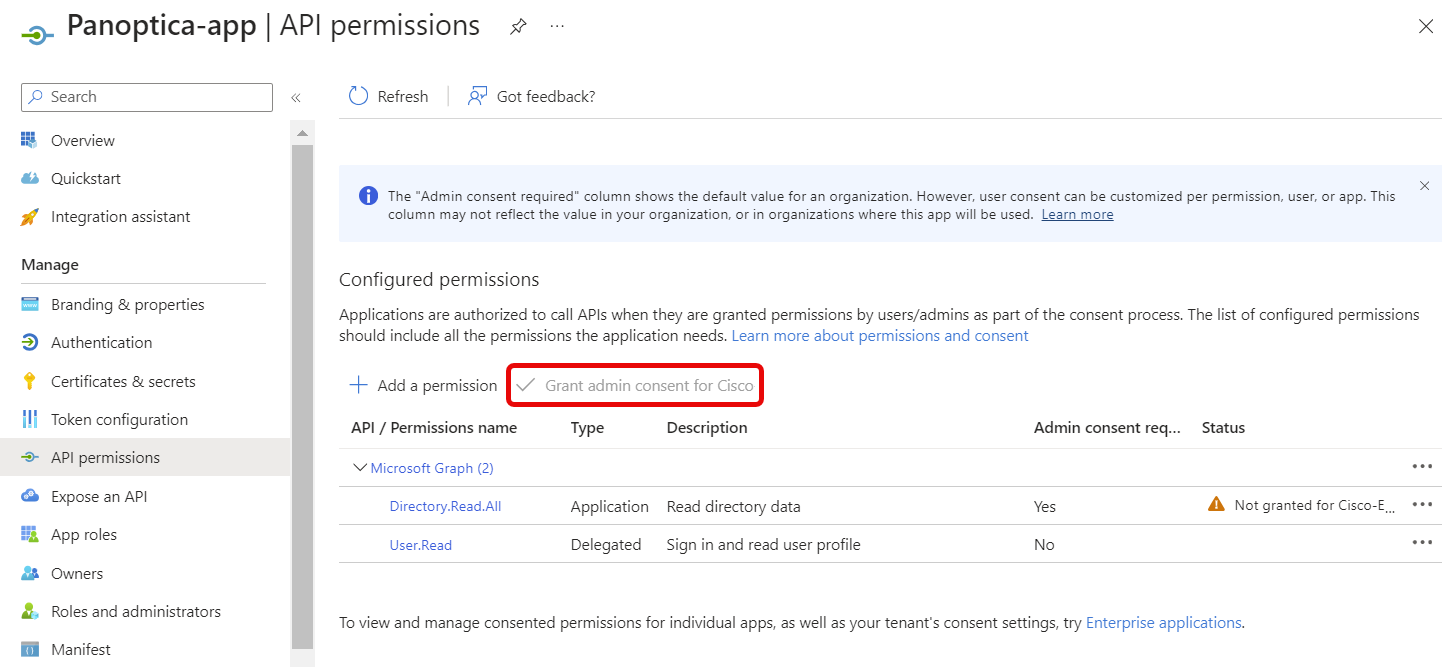
Back on the Panoptica application page in your Azure tenant, click API permissions.
-
Click Add a permission and a new overlay will open on the right.
-
Click the Microsoft Graph option.
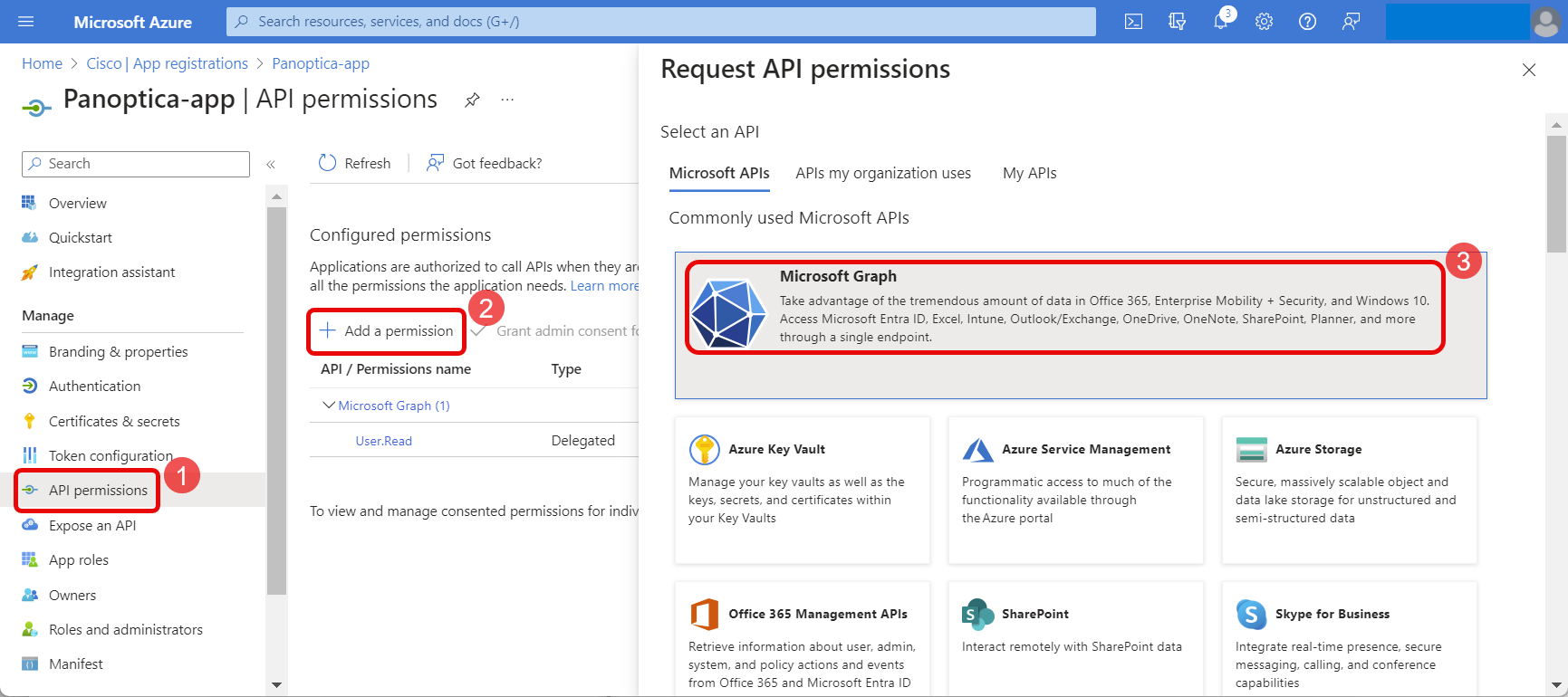
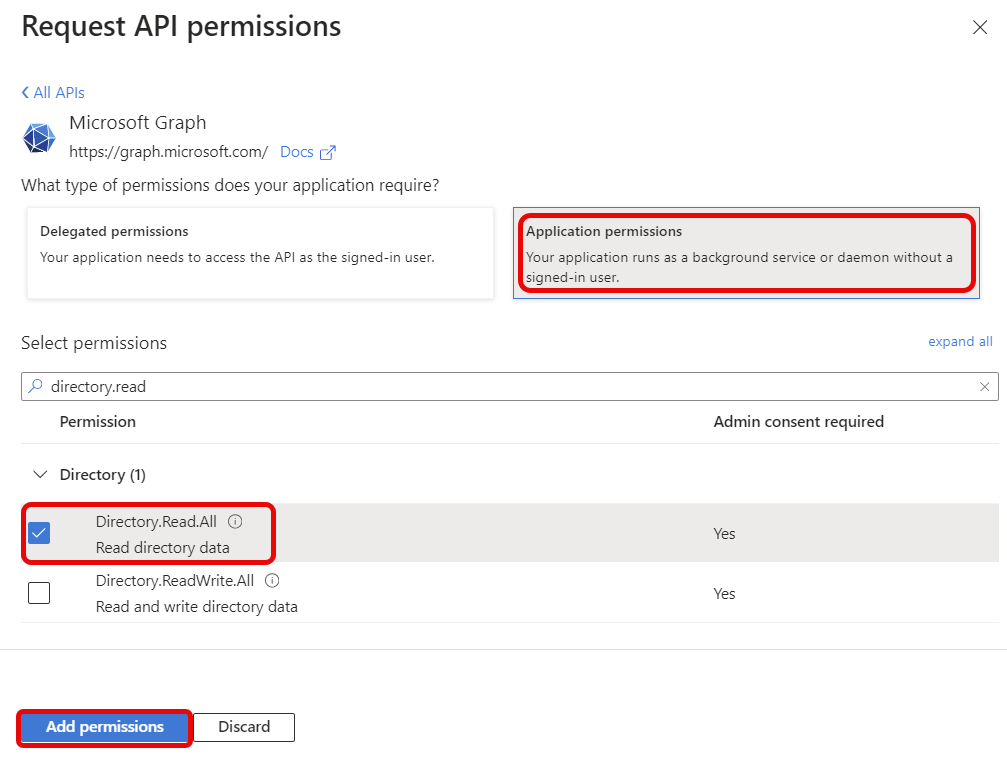
- Click Application permissions to see a list of the permissions that can be added.
Expand > Directory, and select the Directory.Read.All permission below.
Then click Add permissions.
Admin consent requiredAn administrator in your tenant must grant admin consent for the permissions to be granted. Ask an administrator to go to the permission page of your application, and click Grant admin consent for {tenant name}. Until admin consent is granted, the permissions are not effectively added to the application.
Step 3: Assign a Role for Subscriptions
The next step is to assign roles to the app registration created in Step 1 above. If you are enabling CVE and malware scanning, you need to create a custom role to facilitate the creation of an agentless CVE scan infrastructure within your environment. This infrastructure requires permissions for managing resources, including creating and managing compute instances for scanning purposes, as well as network resources for management and communication with our platform.
Also make sure to select Enable CVE & Malware scan on the Azure onboarding screen in the Panoptica console.
If you are not enabling CVE and malware scanning, the built-in Reader role is sufficient for CSPM scans. This role allows listing all customer resources within the target scope (subscription ormanagement group) for analysis on our platform. If you are not enabling CVE and malware scanning, skip this section and continue with Assigning a Role below.
Create the custom role (CVE scanning enabled only):
-
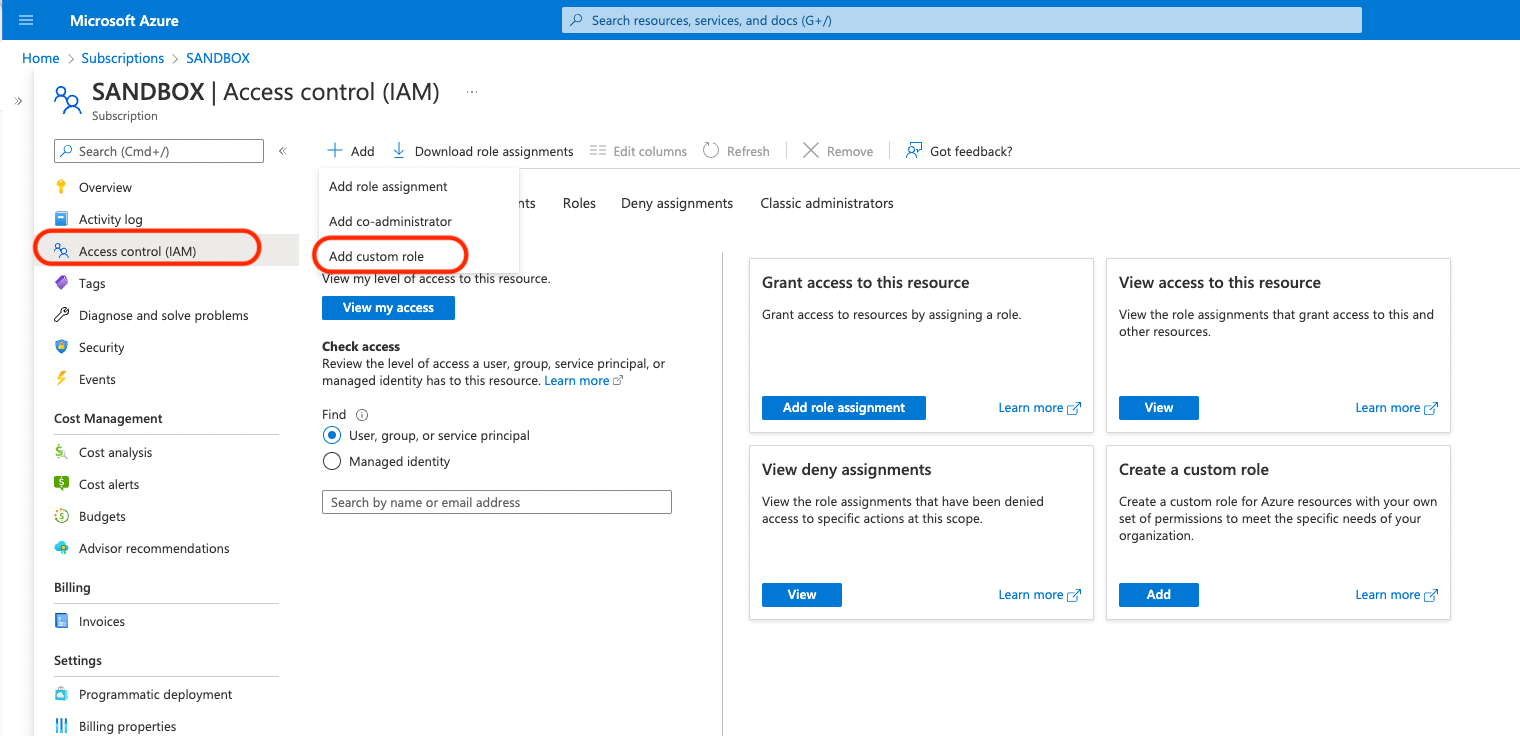
Go to Subscriptions, either from the menu or the search bar. Click on any subscription.
-
Click Access control (IAM). Click Add and choose Add custom role.
-
From the Basics tab, choose Start from JSON as the Baseline permissions option, and upload the
panoptica-CVE-scanning.jsonpolicy below as a JSON file: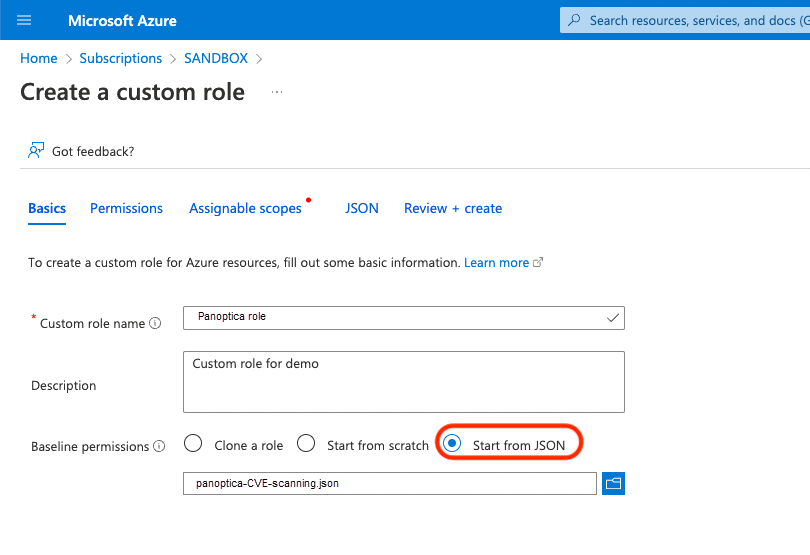
{
"properties": {
"roleName": "panoptica-CVE-scanning",
"description": "Used by Panoptica to scan CVEs",
"assignableScopes": [
],
"permissions": [
{
"actions": [
"*/read",
"Microsoft.Resources/subscriptions/resourcegroups/write",
"Microsoft.Network/virtualNetworks/write",
"Microsoft.Network/virtualNetworks/subnets/write",
"Microsoft.Network/networkInterfaces/write",
"Microsoft.Network/virtualNetworks/subnets/join/action",
"Microsoft.Compute/virtualMachineScaleSets/write",
"Microsoft.Authorization/roleAssignments/write",
"Microsoft.Compute/snapshots/write",
"Microsoft.Compute/virtualMachineScaleSets/virtualMachines/delete",
"Microsoft.Storage/storageAccounts/listKeys/action",
"Microsoft.Storage/storageAccounts/write",
"Microsoft.Compute/galleries/write",
"Microsoft.Storage/storageAccounts/blobServices/containers/write",
"Microsoft.Compute/galleries/images/write",
"Microsoft.Compute/images/write",
"Microsoft.Compute/galleries/images/versions/write",
"Microsoft.Compute/images/delete",
"Microsoft.Compute/galleries/images/versions/delete",
"Microsoft.Compute/snapshots/delete",
"Microsoft.Compute/disks/*",
"Microsoft.Compute/disks/beginGetAccess/action",
"Microsoft.Compute/virtualMachineScaleSets/virtualMachines/*",
"Microsoft.Network/virtualNetworks/subnets/join/action",
"Microsoft.Compute/snapshots/delete"
],
"notActions": [],
"dataActions": [],
"notDataActions": []
}
]
}
}This will fill out the name, description, and relevant permissions of the role. You will be able to change the name and description here.
-
Click the Assignable scopes tab and click Add assignable scopes. From the side panel, choose all subscriptions or management groups that you want to onboard, and click Select.
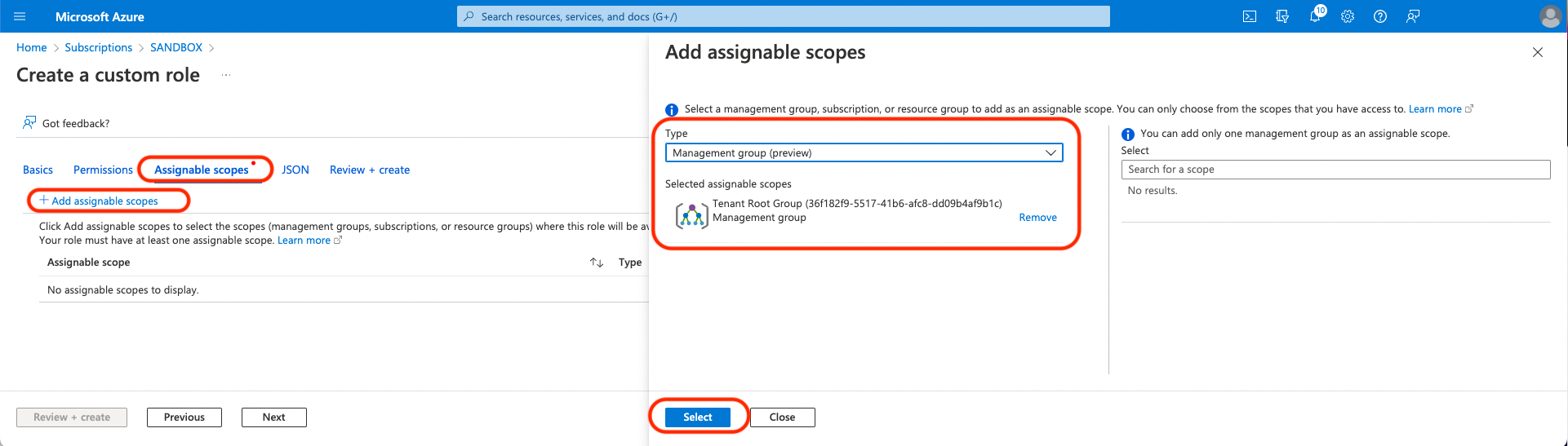
- Using a management group (and specifically the Root management group) is recommended so that the role can be assigned to new subscriptions created in the future.
- Note that you will not be able to onboard a subscription that is not in the assignable scope of this role.
-
Click the Review + create tab, and click Create.
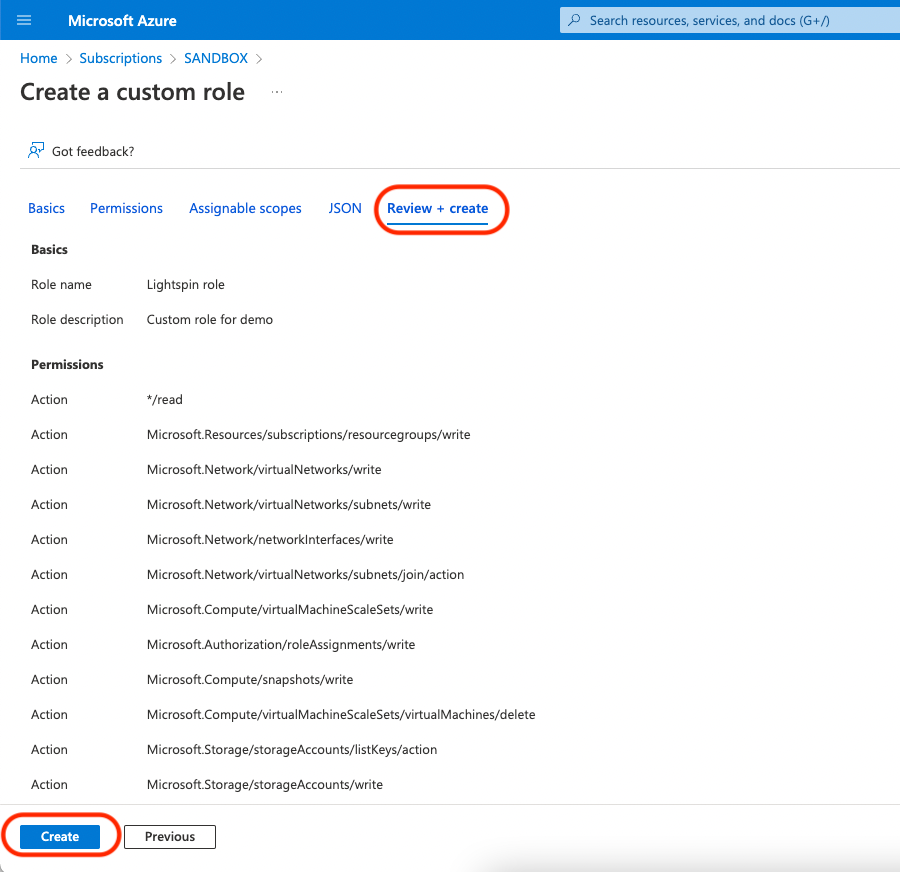
Assigning a Role
-
Choose the scope of resources you want to connect to Panoptica: an entire Tenant/Management Group, or a single Subscription.
- If you want to onboard a specific subscription, go to Subscriptions and click the subscription that you want to onboard.
- If you want to onboard multiple subscriptions, go to Management groups and click the Management group that you want to onboard.
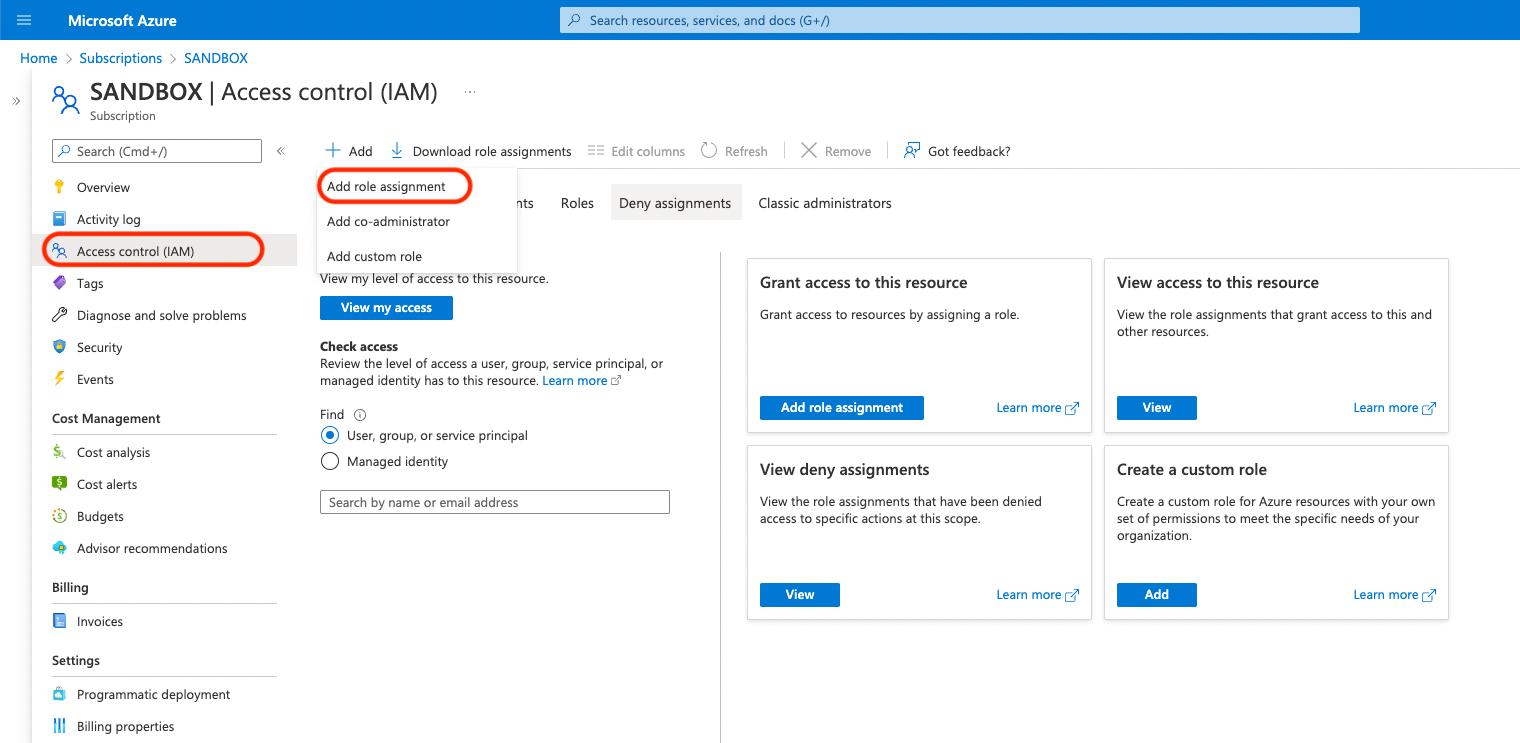
-
Click Access control (IAM). Click Add and choose the Add role assignment option.
-
Search for the relevant role.
- If you are not enabling CVE and malware scanning, select the Reader role and click Next.
- If you are enabling CVE and malware scanning, you need to select both the custom role you created above, as well as the Reader role:
- Select the custom role and then click Next.
- Select the Reader role and click Next.
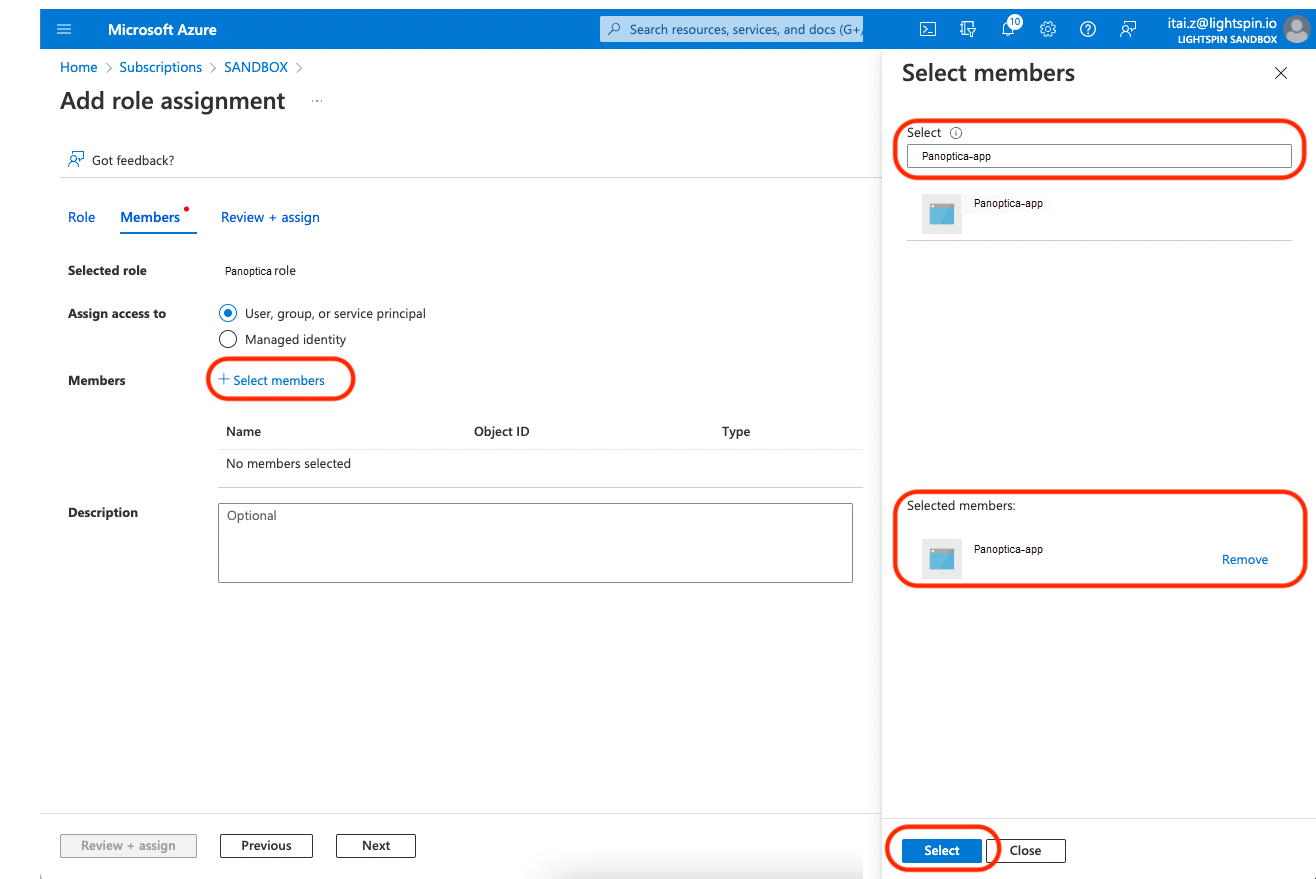
-
Click the Members tab. Make sure the Assign access to option is User, group, or service principal, and click + Select members. From the side panel, look for the Panoptica application you created in Step 1 and click on it, and then click Next.
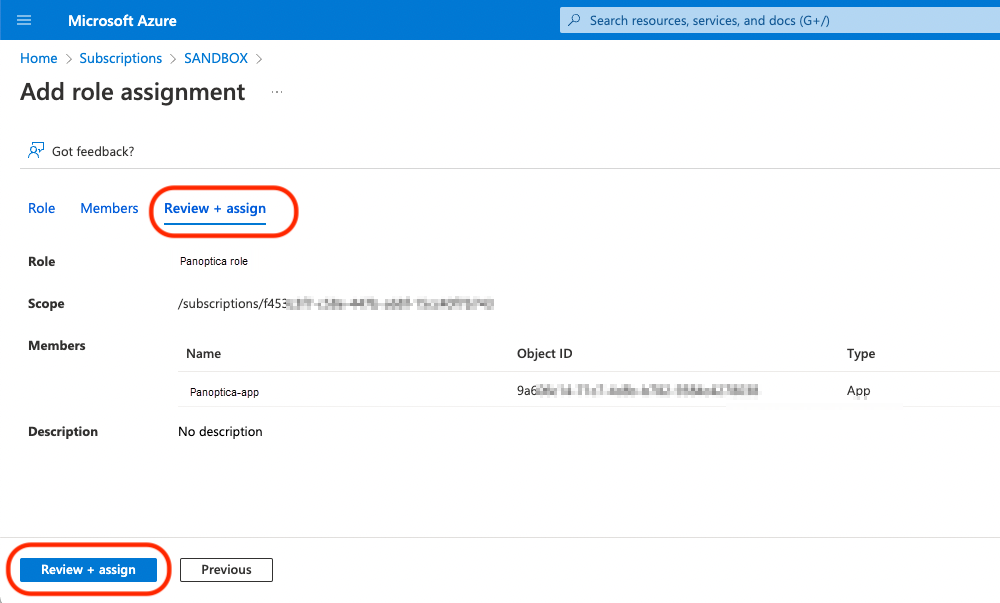
-
Click the Review + assign tab, and click Review + assign.
Step 4: Finish onboarding
That's it! You're done with the Azure configuration. Now you just have to complete the onboarding in Panoptica's console UI.
- Open a new tab and log into Panoptica. Browse to the Microsoft Azure onboarding page, which you'll find on the Accounts tab in the Settings pane.
- Enter the identifiers you retrieved when creating the application into the relevant fields on the Azure onboarding page:
- Directory (or tenant) ID
- Application (or client) ID
Retrieving identifiersIf you don't have those identifiers available for whatever reason, you can find them again in your Azure portal.
Browse to Microsoft Entra ID → App Registrations → <name of your-panoptica-app>.
On the default Overview tab, you'll find them under Essentials.
-
If you chose to enable CVE scanning, make sure you have selected the Enable CVE & Malware scan option.
CVE Scan role reminderIf you enabled CVE scanning in the Panoptica console, make sure you create the custom
panoptica-CVE-scanningrole as detailed above, and assign it to the relevant subscription.
- Now click Check Credentials to make sure everything is in order.
- If it is, click Finish and Start Scan. The new account will appear in the list of accounts after a few moments, and all of the subscriptions that the application has permissions for will be onboarded and scanned.
ResourcesPanoptica creates infrastructure in about two dozen Azure regions around the world to support the scans. The infrastructure consists of a resource group, a virtual network (VNet), a subnet, a network interface (NIC), and a scale set. This comprehensive framework is crucial to ensure we have all necessary assets for scanning your resources.
We launch 10 VMs at a time on this infrastructure to scan your resources. If there are still messages in the queue, we request additional VMs – 10 at a time – until the queue is empty. All transient assets (VMs, disks, snapshots) are deleted once the scan is finished; the infrastructure remains for the next scan.
Updated 5 months ago