Risk Categories
The Risk Categories on the Security Posture page illustrate the distribution of detected risks across different categories. Each category's proportion is calculated based on the number of risks detected out of the total number of potential risks the system can detect in that category. This provides insight into which areas are most impacted by security issues and helps prioritize remediation efforts accordingly.
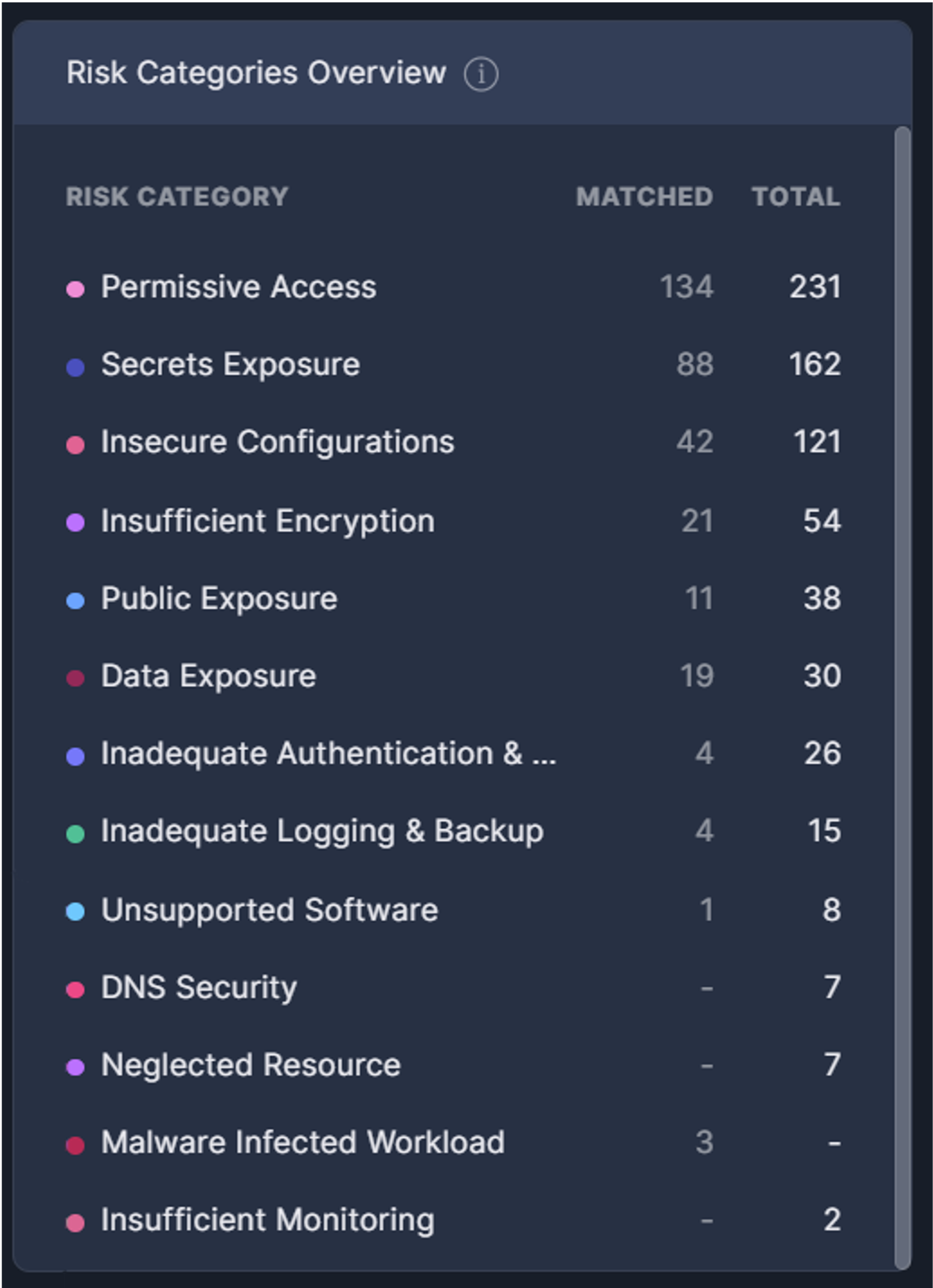
Panoptica identifies the following risk categories:
- Data Exposure
Storage, databases, and cloud analytics services that can be accessed by unauthorized entities. - DNS Security
A misconfiguration that can allow an attacker to perform a subdomain takeover, usually caused by a DNS that is not directing to any resource on the cloud side. - Inadequate Authentication & Authorization
Weak or insecure authentication methods that can result in compromised identities. - Inadequate Logging & Backup
Lack of recording system or application activities and insufficient backup that can compromise data recovery capabilities. - Insecure Configuration
Unencrypted objects or databases, insecure network settings, backups not enabled, dangerous defaults, risky and weak configurations, or other misconfigurations resulting from human error. - Insufficient Encryption
Inadequate or missing encryption that can expose data to unauthorized access or interception. - Insufficient Monitoring
Inadequate or incomplete logs and audit trails for access or management actions, such as configuration changes, permissions changes, and data manipulation. - Malware Infected Workload
Panoptica leverages third-party threat intelligence to identify any anomalies and real-time threats. - Neglected Resource
Resources in your cloud environment that are unused or not associated to any other resource. - Permissive Access
Excessive permissions that could allow users to escalate their privileges in the system. - Public Exposure
Storage, databases, or other resources that are hosted on a public cloud. - Secret Exposure
Exposed credentials, such as unencrypted passwords, access keys, API keys and tokens, or SSH keys. - Unsupported Software
Software that has reached End of Life (EoL), or End of Support (EoS).
For a complete list of the risks and security issues that Panoptica can identify, see the Risk Findings Catalog.
Updated 5 months ago