Use Cases for Dashboard
Panoptica Dashboard makes cloud security management more effortless by supporting a wide range of use cases. The table below describes some of the prominent use cases, detailed instructions, and why we love them.
Use Case | How-to-use | Why we built it |
|---|---|---|
Review the new attack paths in the Trend widget |
| Review critical data about your cloud environment in an intuitive way. DevSecOps teams can use trends to track progress and changes occurring in the cloud. |
Identify a runtime event |
| Responding in a timely manner is crucial to prevent the attacker from causing further damage, stealing sensitive information, or using the compromised system for other malicious activities. The longer an attack goes undetected, the more difficult and costly it becomes to remediate. |
Review the number of critical attack paths and what risks they pose |
| Prioritize your security efforts based on the potential impact of each attack path. Critical attack paths pose the highest level of risk to the organization's systems, data, and reputation, and therefore require immediate attention. By understanding the risks posed by critical attack paths, you can take proactive measures to mitigate those risks and improve the overall security posture. |
Focus on exposed secrets and review the detected attack paths severity |
| Prioritize your efforts to mitigate potential threats based on the severity of the attack paths. By understanding the potential impact of each attack path, your team can focus their resources on the most critical areas and take appropriate measures to prevent or mitigate the risks. |
Remediate multiple attack paths caused by the AWS Managed Policy AmazonS3FullAccess via Panoptica Guardrails Policy |
| Utilize Prioritization funnel to easily remediate most critical attack paths effortlessly. In this case, deny guardrails are dynamic policies generated by the platform to reduce the risks discovered. The guardrails do not change existing policies. The guardrails eliminate the attack vectors found, such as privilege escalation, by denying the risky actions only for specific resources. |
Analyze compliance with major frameworks |
| Meet the necessary regulatory and legal obligation by reviewing the compliance with major frameworks and implement the necessary controls to protect your data in the cloud. |
Dissect Privilege Escalation attack path by risk engine and severity |
| Review the attack paths in the context of root causes, risk severity and number of attack paths. This features provides further visibility into the cloud environment and reduces the number of alerts needed to be reviewed. |
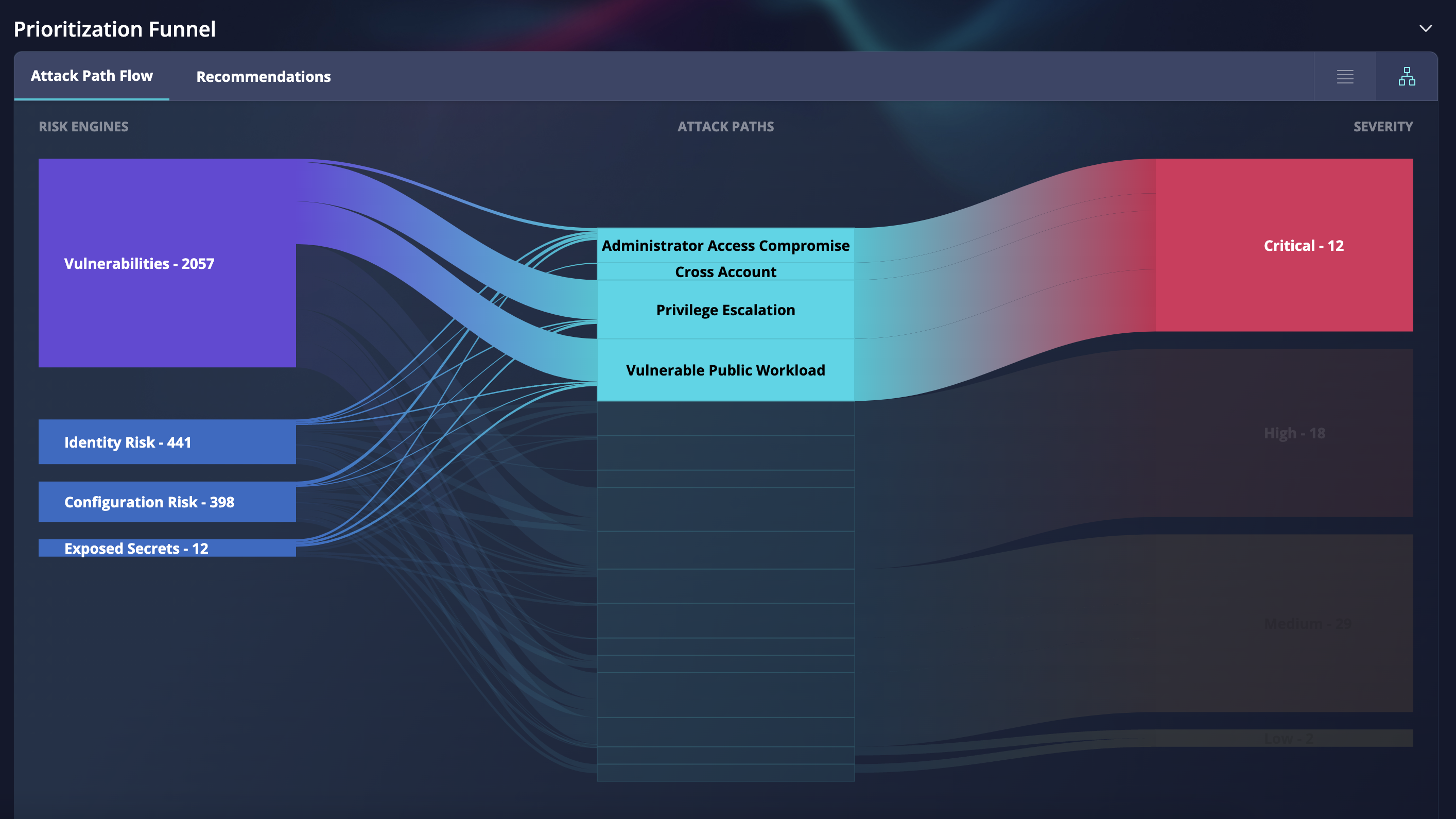
Fig 1. The use case for the prioritization funnel to review the number of critical attack paths and what risks they pose
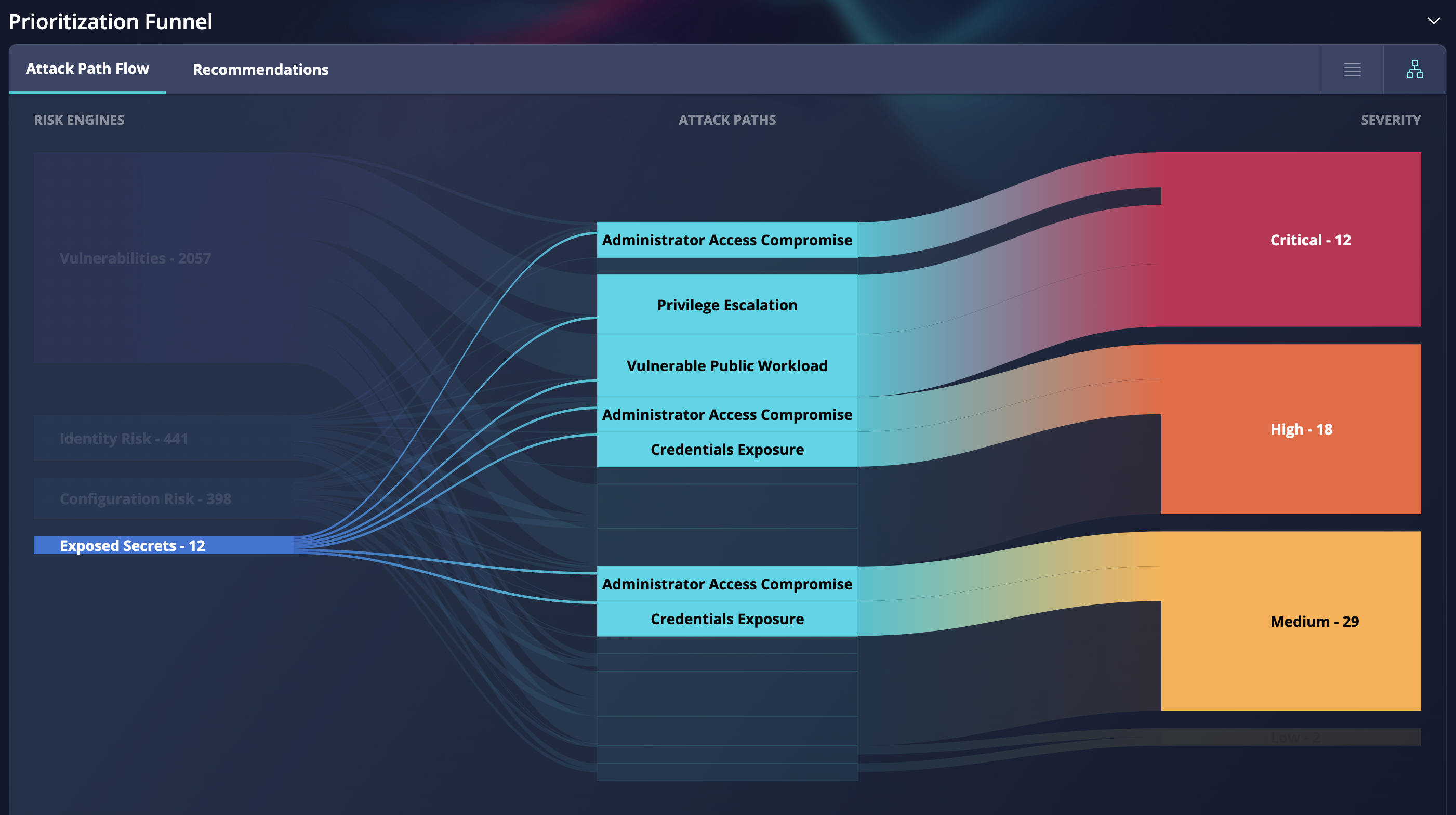
Fig. 2 The use case for the prioritization funnel to focus on exposed secrets
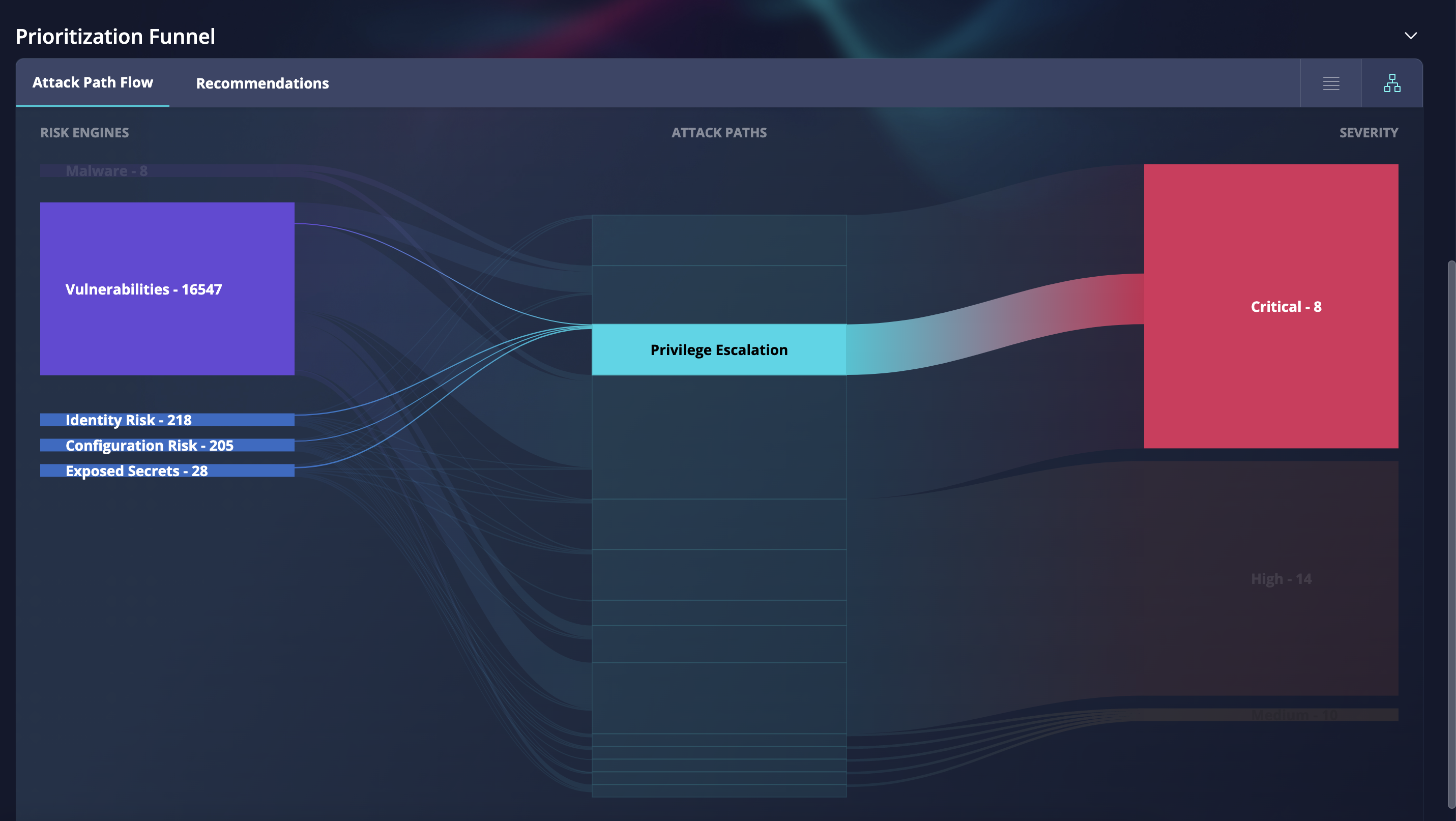
Fig. 3 The use case for the prioritization funnel to dissect your attack path by the risk engines and the risk severity
Updated 5 months ago