Use Case for Attack Path Analysis
Attack Path Example: Public EC2 Instance with Strong Role
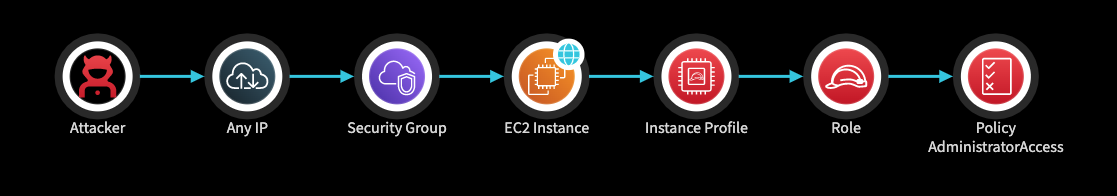
An EC2 instance can be public though a direct attached public IP address. In addition to having a public IP address, Panoptica evaluates the inbound rules of the attached security groups, as well as the relevant ACL rules. In the attack path below, the EC2 instance is publicly exposed through a public IP address and the attached security group includes an inbound rule that allows access from any IP (0.0.0.0/0).
An EC2 instance can also be publicly exposed through a public load balancer. In the attack path below, the EC2 instance is publicly exposed by direct public IP and by public load balancer.
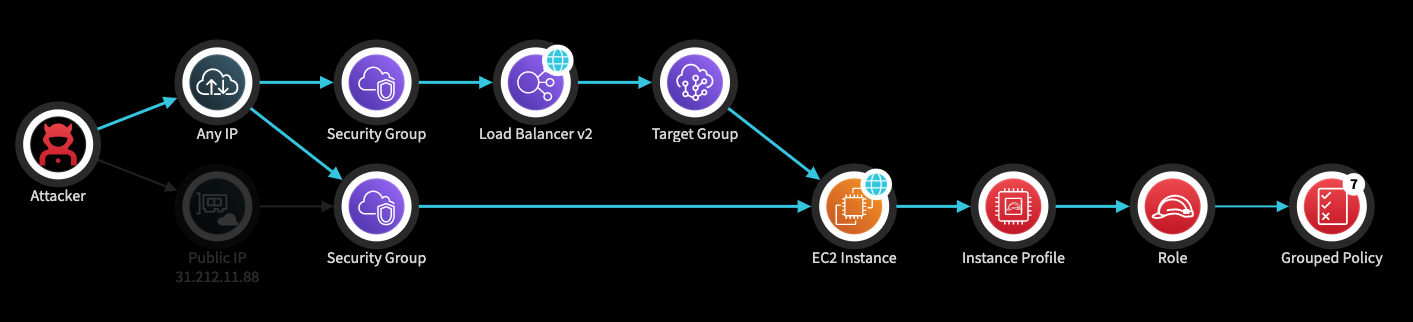
The EC2 instance is both public and has a strong role attached.
The risk here is that an external attacker can access the service that runs on the EC2 and use an exploit to reach the underlying layer. For example, if there is a web application running on the EC2, an attacker can exploit an application vulnerability such as RCE, XXE, SSRF and more, to access the Instance Metadata Endpoint. Though the Instance Metadata Endpoint, an attacker might get the credentials of the role attached to the EC2 instance and use them.
If the attached role is strong, the attacker's permissions will be strong as well.
Updated 5 months ago