CI/CD CLI Tool
Panoptica enables you to shift left your security by downloading a Command Line Interface (CLI) to proactively detect risks in your CI/CD pipelines. Integrating the Panoptica CI/CD CLI tool into the development workflow enables you to scan container images for potential security vulnerabilities. Panoptica CI/CD CLI tool can detect and block security issues pre-production, before they are merged into the main codebase and deployed to production environment.
Installation
In order to integrate Panoptica into your development workflow, you need to download the Panoptica CI/CD CLI tool, and generate an API Key. You'll find download links, configuration details, examples, and more for each version listed in the table below.
CLI Version | Features |
|---|---|
Adds the ability to scan secrets. | |
Adds the ability to scan Infrastructure as Code (IaC) directories. | |
Adds the ability to specify a region (US or EU). | |
Adds the ability to configure custom policies. | |
Initial release |
Generate API Key
In order to send CLI scan results to the Panoptica console UI, you need an API Key. To generate the key, log into the Panoptica platform and select Settings in the navigation pane, then the API Keys tab.
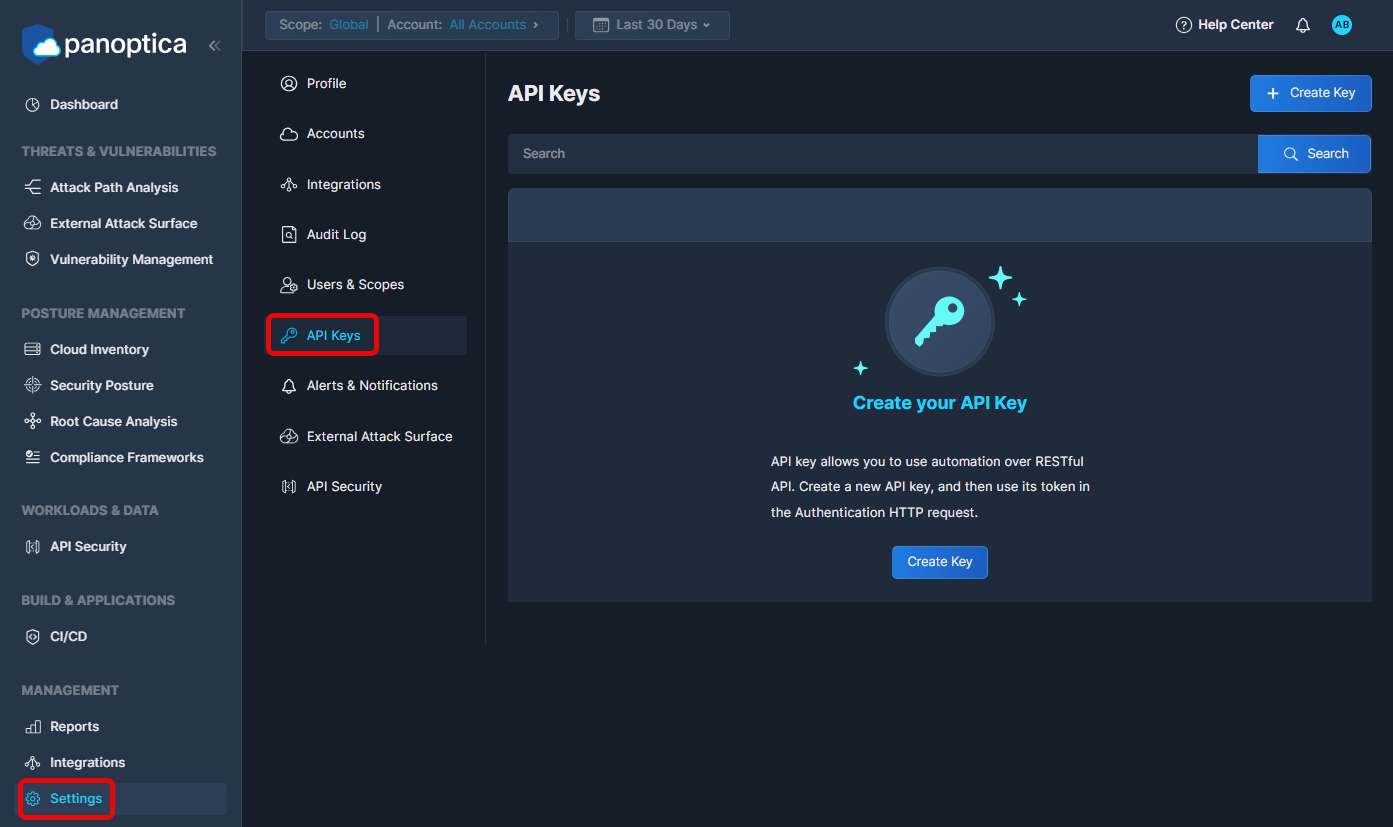
Click Create Key to open a popup overlay, where you can generate the key.
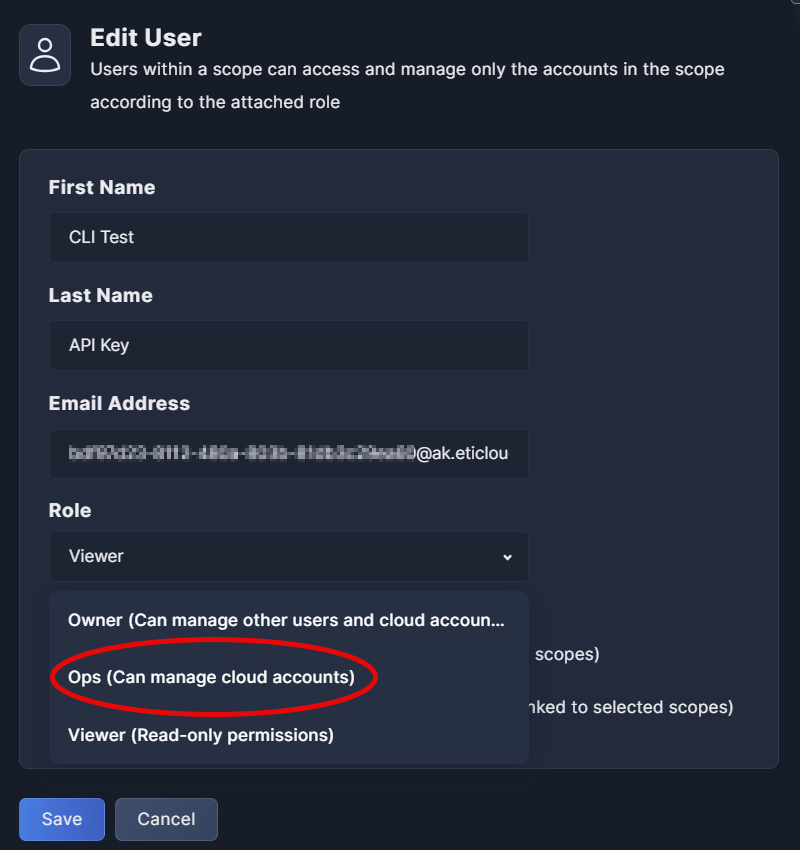
Permissions requiredUsers must have an Owner or Ops role in Panoptica to generate API Keys.
See User Management for details on User Roles
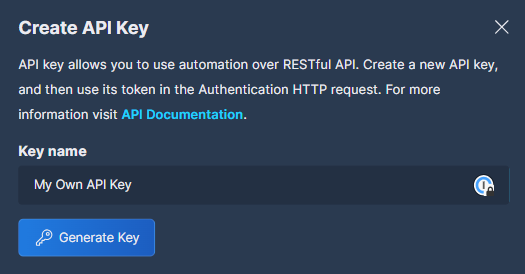
Enter a logical Key name, and click Generate Key.
Promote API Key to Ops userOnce the API Key is created, go to the Users & Scopes tab and modify its role from Viewer to Ops. This will enable the key to send scan results to the Panoptica console UI.
See User Management for details on User Roles
Updated 5 months ago